Running Jobs in Docker Containers
Run jobs inside Docker containers orchestrated by Semaphore.
Overview
Jobs can run inside Docker containers. This allows you to define a custom-built environment with pre-installed tools and dependencies needed for your project. You can enable this setting in the pipeline agent or in the block agent override.
You can run multiple containers at the same time. The job runs in the first container (called main) and attaches the other containers to the same network. This is similar to how containers inside a Kubernetes pod communicate.
The network addresses of all containers are mapped to their names. Let's say you have two containers, "main" and "mysql", you can connect to the database from the main container with:
mysql --host=mysql --user=root
How to run jobs inside Docker containers
To run the job inside a Docker container you must define at a Docker image in your agent configuration.
The following example shows how to set up two containers:
- main: where the commands of the job are executed. The container is running an Ubuntu 20.04 container. The image is pulled from the Semaphore Container Registry
- web: runs an nginx container and attaches it to the same network as the main container
- Editor
- YAML
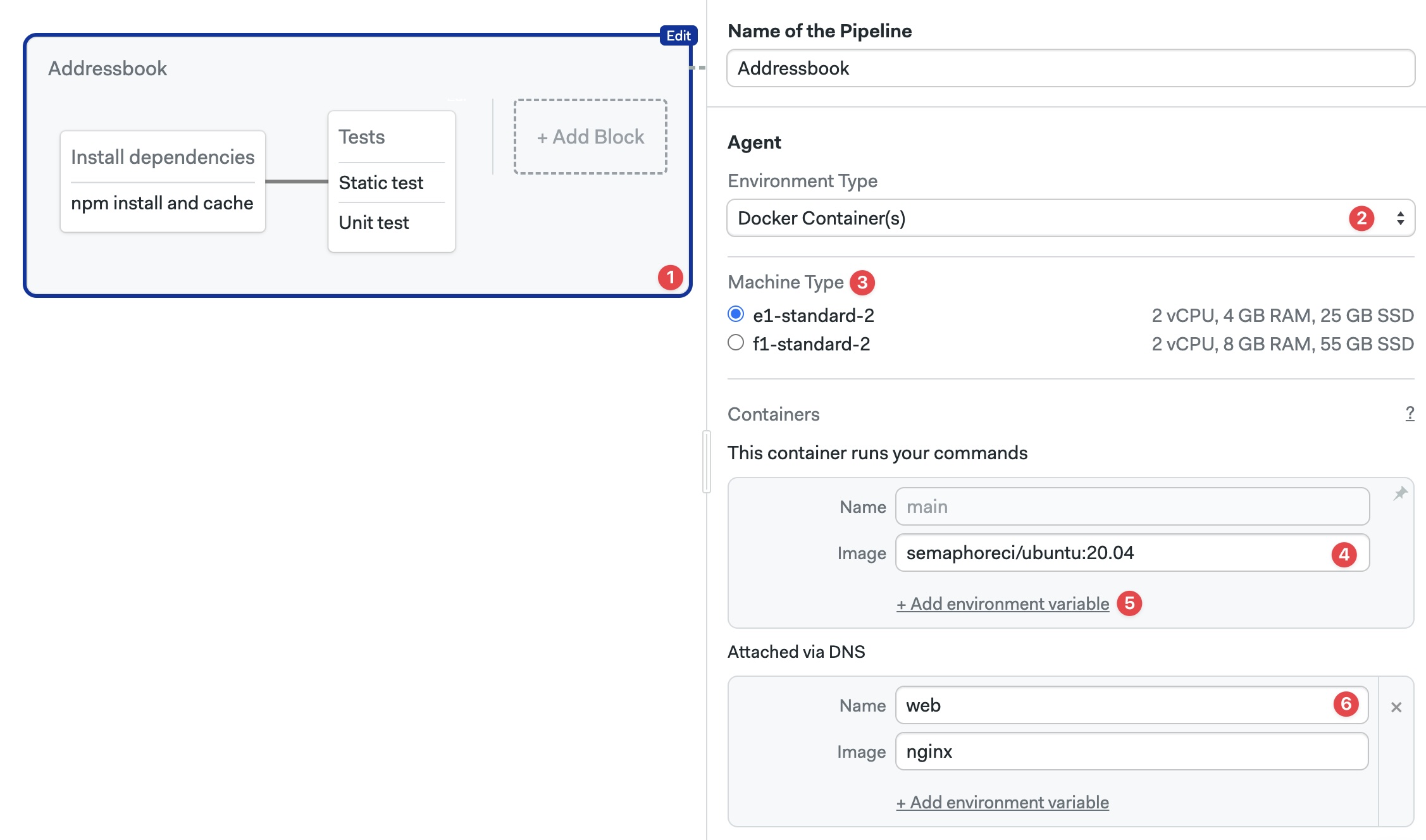
Follow these steps to configure Docker containers using the workflow editor:
- Select the pipeline
- In Environment Types select Docker Container(s)
- Select the machine type
- Type the Image name for this container
- Optionally, add environment variables
- Optionally, add more containers
Follow these steps to configure Docker containers using the YAML container definition:
- Add the
agentandmachine - Add a
containerskey - Each list item is a container. The first one must be called
main - Add the
image - Optionally, add
env_vars - Optionally, add more containers
version: v1.0
name: Initial Pipeline
agent:
machine:
type: e1-standard-2
os_image: ubuntu2404
containers:
- name: main
image: 'semaphoreci/ubuntu:20.04'
env_vars:
- name: FOO_1
value: BAR_1
- name: web
image: nginx
blocks:
- name: 'Block #1'
dependencies: []
task:
jobs:
- name: 'Job #1'
commands:
- 'curl http://web'
Pulling Images from Private Docker Registries
If the images you need for your Docker environment are not publicly available, you need to provide authentication credentials in your pipeline. This feature is only available by editing the pipeline YAML directly.
See containers in pipeline YAML for more details.
Images in Docker Hub
To pull images from a private Docker Hub registry, follow these steps:
-
Create a secret with the following key-value pairs:
DOCKER_CREDENTIAL_TYPE=DockerHubDOCKERHUB_USERNAME=<your Docker Hub account username>DOCKERHUB_PASSWORD=<your Docker Hub account password>
-
Import the secret by name into the agent using
image_pull_secret. The following example assumes the secret is calleddockerhub-pull
agent:
machine:
type: e1-standard-2
containers:
- name: main
image: <your-private-repository>/<image>
image_pull_secrets:
- name: dockerhub-pull
Images in AWS ECR
To pull images from a private AWS Elastic Container Registry (ECR), follow these steps:
-
Create a secret with the following key-value pairs:
DOCKER_CREDENTIAL_TYPE=AWS_ECRAWS_REGION=<aws-ecr-region>AWS_ACCESS_KEY_ID=<your-aws-access-key>AWS_SECRET_ACCESS_KEY=<your-aws-secret-key>
-
Import the secret by name into the agent using
image_pull_secret. The following example assumes the secret is calledecr-pull
agent:
machine:
type: e1-standard-2
containers:
- name: main
image: <your-private-repository>/<image>
image_pull_secrets:
- name: ecr-pull
Images in Google GCR
To pull images from a private Google Container Registry (GCR), follow these steps:
-
Create a secret with the following key-value pairs:
DOCKER_CREDENTIAL_TYPE=GCRGCR_HOSTNAME=gcr.io
-
Download the service account keyfile that provides access to your Google Container Registry.
-
Upload the keyfile to the secret created on step 1
Important: the file must be mounted on
/tmp/gcr/keyfile.json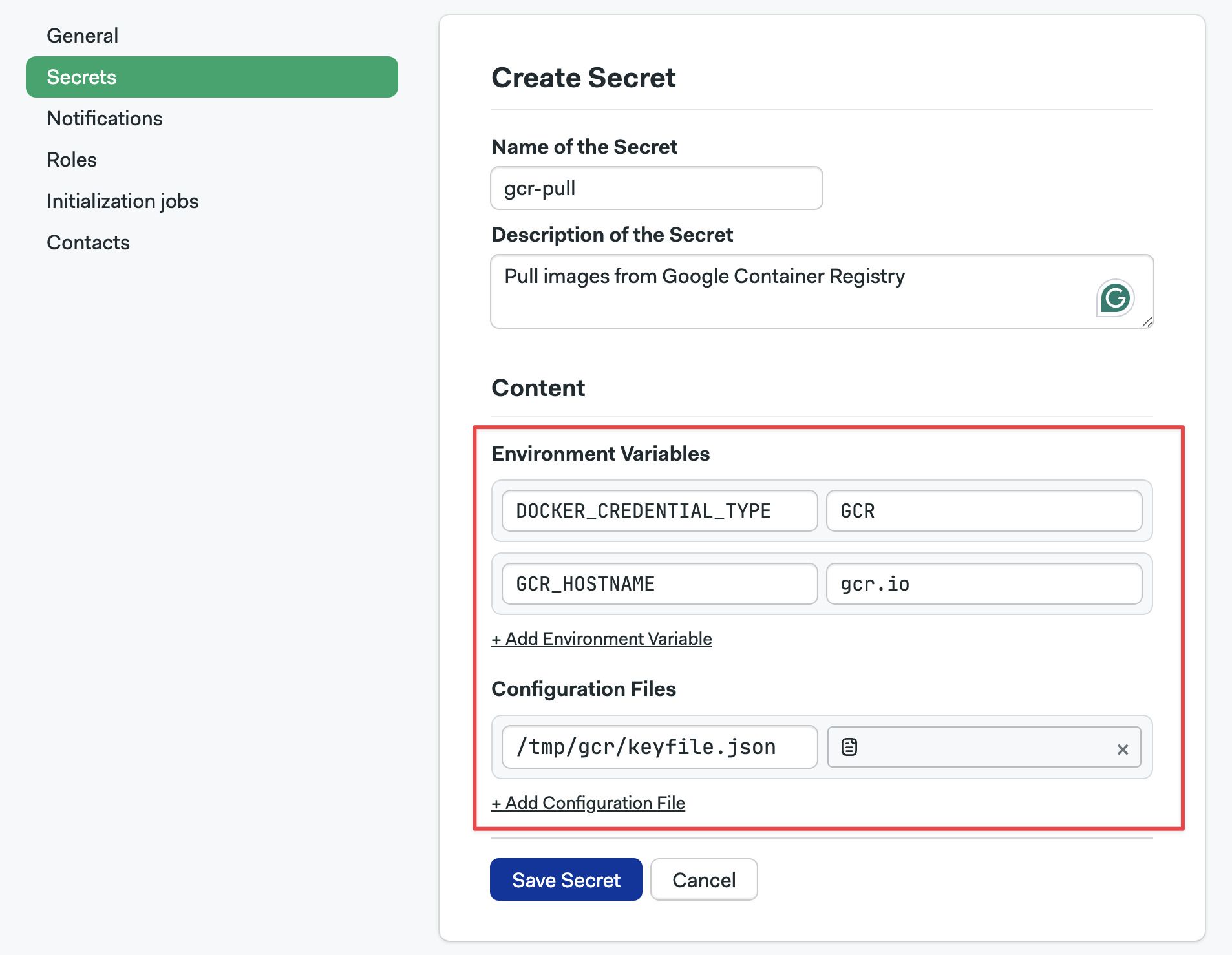
-
Import the secret by name into the agent using
image_pull_secret. The following example assumes the secret is calledgcr-pull
agent:
machine:
type: e1-standard-2
containers:
- name: main
image: <your-private-repository>/<image>
image_pull_secrets:
- name: gcr-pull
Images in Quay.io
To pull images from a private Quay.io registry, follow these steps:
-
Create a secret with the following key-value pairs:
DOCKER_CREDENTIAL_TYPE=GenericDockerDOCKER_URL=quay.ioDOCKER_USERNAME=<your-quay-username>DOCKER_PASSWORD=<your-quay-password>
-
Import the secret by name into the agent using
image_pull_secret. The following example assumes the secret is calledquay-pull
agent:
machine:
type: e1-standard-2
containers:
- name: main
image: <your-private-repository>/<image>
image_pull_secrets:
- name: quay-pull
Images in generic registries
To pull images from any arbitrary Docker registry, follow these steps:
-
Create a secret with the following key-value pairs:
DOCKER_CREDENTIAL_TYPE=GenericDockerDOCKER_URL=<your-repository-url>DOCKER_USERNAME=<your-registry-username>DOCKER_PASSWORD=<your-registry-password>
-
Import the secret by name into the agent using
image_pull_secret. The following example assumes the secret is calledregistry-pull
agent:
machine:
type: e1-standard-2
containers:
- name: main
image: <your-private-repository>/<image>
image_pull_secrets:
- name: registry-pull